Today’s cyberattack risks are higher than ever before, and businesses need proactive measures to keep their information secure. Adding even one layer of additional protection can increase your security posture significantly. Multi-Factor Authentication (MFA) eliminates the risk of having a single-entry point to your data, and yet many organizations have not taken the step to enable it
Enable MFA for all users, data, and devices across your entire organization, not just for particular applications or a specific network. Consider MFA to be a part of your cybersecurity puzzle, not the key to the entire cybersecurity kingdom. Enabling MFA for every member of your organization on every device and access point reduces your chances of falling victim to ransomware or a cybersecurity attack.
Use the 1 2 3 Rule of Thumb when it comes to MFA
1. POSSESSION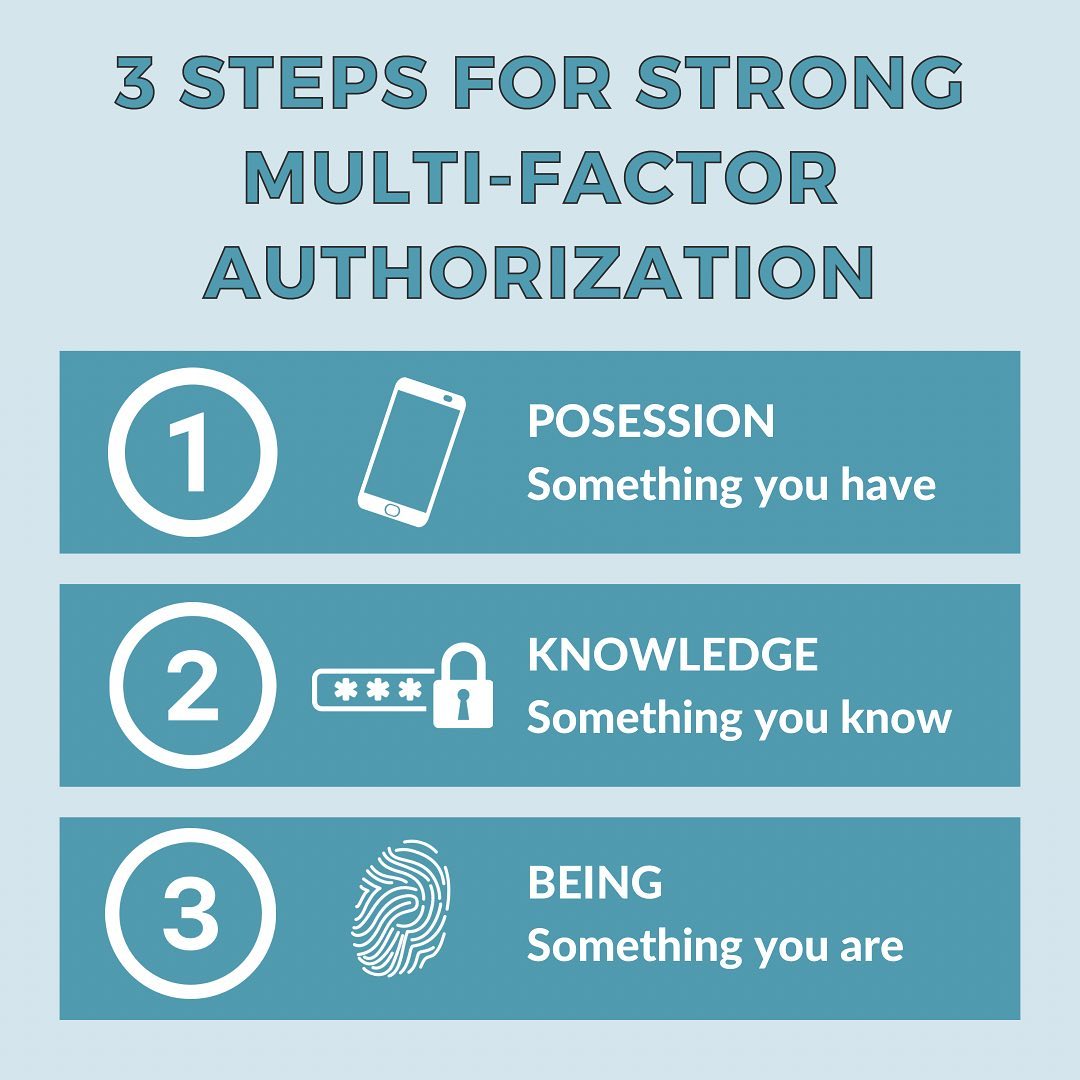 : Use something you have in your possession (a cell phone, second computer, iPad) as a way to send a login code or confirmation code to that device in the event of a data breach or hacking attempt.
: Use something you have in your possession (a cell phone, second computer, iPad) as a way to send a login code or confirmation code to that device in the event of a data breach or hacking attempt.
2. KNOWLEDGE: Use something that only you know to build your security questions and/or passwords. Don’t create patterns with your passwords. For instance, avoid creating passwords that all start with the same word or phrase, where just the ending is changed. Individuals are not sleuthing your passwords; algorithms are. Don’t make it easy.
3. BEING: One thing that a hacker cannot compete with is your fingerprint, face scan or other bio setting. When possible, create logons with fingerprints or facial recognition counts.
Consider all the areas of your life where MFA needs to be implemented.
Work and personal emails, cell phones, online banking, PayPal, Venmo, Amazon, Facebook, Instagram, and any app with a card or bank account associated with it.
Setting up a multi-factor authentication (MFA) solution is a great first step to take, but your protection shouldn’t end there. For more details about cybersecurity measures you can take today contact us at Radiant Resources. We are here to help organizations like yours prepare, protect, detect, respond and recover along all points of the cybersecurity lifecycle.

